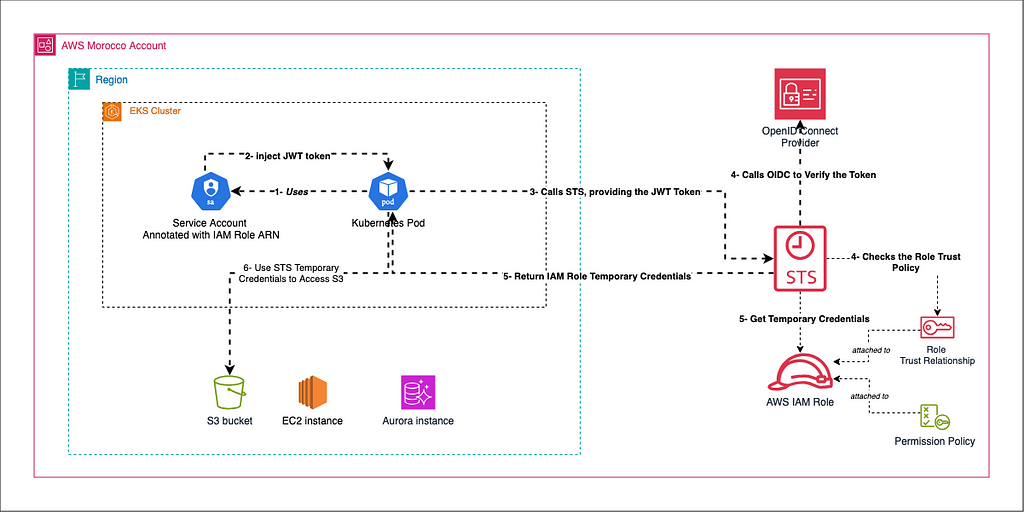
AWS IAM Roles For Kubernetes Service Accounts (IRSA)
In the world of Kubernetes and AWS, managing access to AWS resources from your Kubernetes cluster can be tricky. That’s where AWS IAM Roles for Service

In the world of Kubernetes and AWS, managing access to AWS resources from your Kubernetes cluster can be tricky. That’s where AWS IAM Roles for Service

OpenTofu is a new open source tool for Infrastructure-as-Code (IaC) management across multiple cloud providers, created by the community following the [terraform licence change by
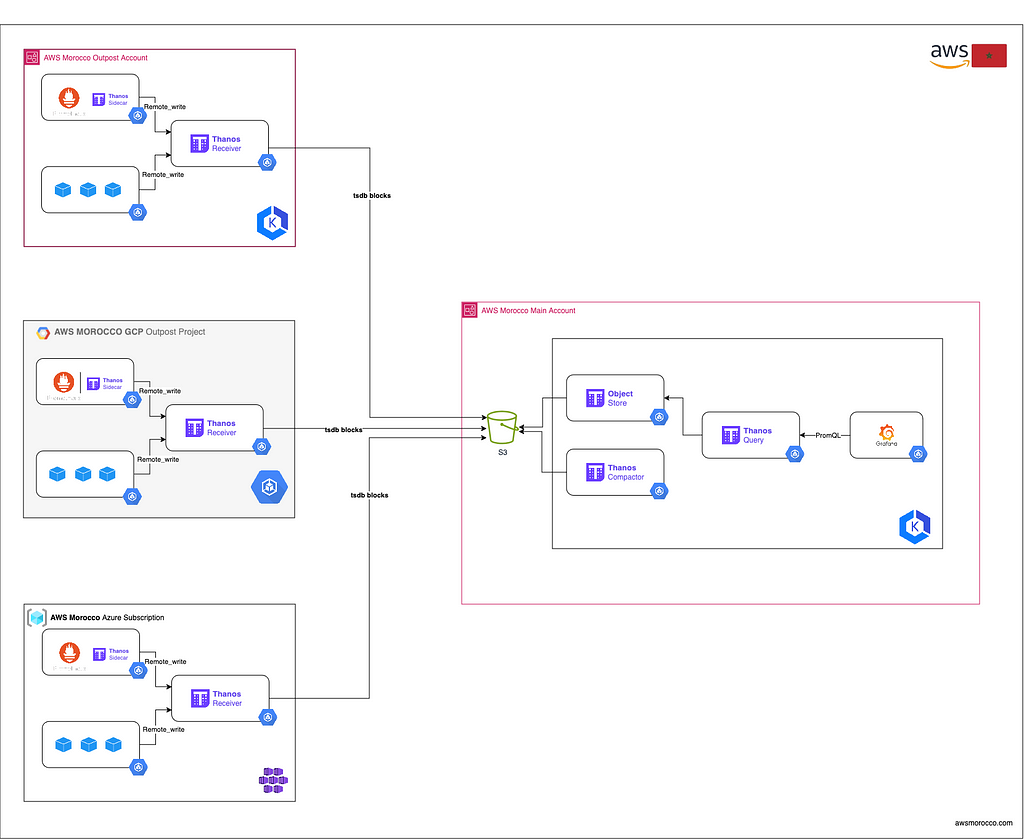
Monitoring large-scale, multi-cloud Kubernetes environments can be a hard task, especially when dealing with high-cardinality metrics and long-term data

In the ever-evolving world of cloud computing, where efficiency and productivity are paramount, developers and DevOps engineers often find themselves navigating the complexities of AWS infrastructu…
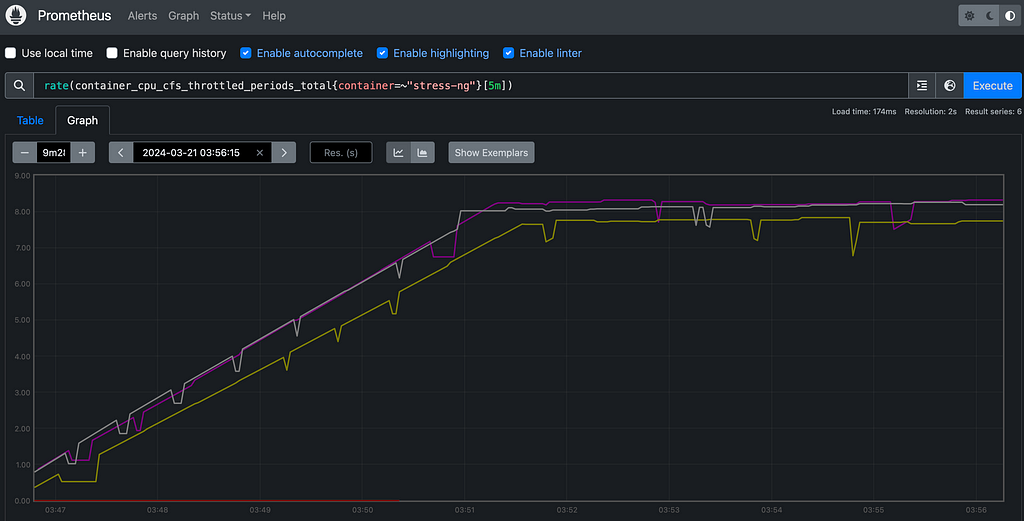
As Kubernetes administrators and developers, we’ve all heard the notion that pods can get evicted due to high CPU pressure on a node. But is this really
In Terraform, drift detection helps spot any mismatches between the infrastructure you’ve outlined in your code and what’s actually out there running in your cloud accounts. This is super important…

In the world of cloud networks, security and confidentiality are crucial. [AWS PrivateLink](https://docs.aws.amazon.com/vpc/latest/privatelink/what-is-

Dear AWS Enthusiasts,
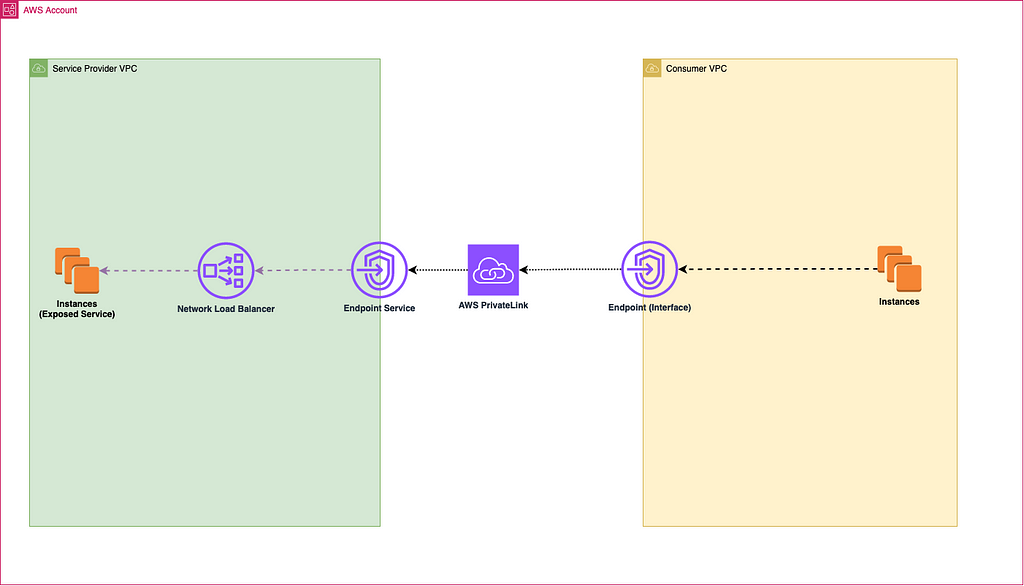
AWS PrivateLink provides a secure and reliable way to connect VPCs within the same region, but it doesn’t directly support connections between VPCs in different regions. To address this limitation,…

Container Storage Interface (CSI) drivers play a crucial role in managing persistent storage for containerized applications. When working with Amazon Elastic Kubernetes Service (EKS), integrating C…