How Does AWS PrivateLink Work ?

In the world of cloud networks, security and confidentiality are crucial. [AWS PrivateLink](https://docs.aws.amazon.com/vpc/latest/privatelink/what-is- privatelink.html) is an essential service that bridges the gap between service exposure and network security in an elegant way. By providing a private connection to services hosted on AWS, PrivateLink ensures that traffic between your VPC and the services you consume does not traverse the public internet. This not only increases security, but also reduces exposure to potential threats and improves network latency.
The aim of this article is twofold. First , we’ll break down how AWS PrivateLink works, highlighting its underlying mechanisms and explaining why it’s becoming an essential part of the AWS secure architecture. Next , we’ll demonstrate a practical configuration: deploying a simple Flask application endpoint securely using AWS PrivateLink. By the end of this read, you’ll have a complete understanding of PrivateLink and a step-by-step guide to leveraging its capabilities for your own services.
What’s AWS PrivateLink ?
AWS PrivateLink is a network service provided by AWS that enables customers to access services across the AWS network in a secure and scalable manner. PrivateLink is built around the concept of service endpoints. These are provisioned in your VPC and act as a secure entry point to services hosted on AWS or on-premises. Using AWS PrivateLink, services are exposed via the AWS network backbone, rather than the public internet, increasing security and reducing exposure to common threats such as DDoS attacks.
PrivateLink addresses several of the most critical issues in cloud networking:
- Security : it secures network traffic by ensuring it never leaves the Amazon network, significantly reducing the risk of interception or exposure.
- Data exposure : By avoiding the public Internet, PrivateLink limits data exposure, providing a more controlled environment and reducing the attack surface.
- Network complexity : PrivateLink simplifies networking architecture by eliminating the need for Internet gateways, NAT devices and VPN connections for access to private services.
- Scalability : PrivateLink is designed to be highly scalable and manage the throughput and connections required without customers having to manage the underlying infrastructure.
Compared to standard public endpoints, PrivateLink offers a number of advantages:
- Low latency : Because traffic is routed within the AWS network, latency is often lower than if data were routed over the public internet.
- Consistency : Network performance is more consistent because it is not subject to the variable conditions of the public Internet.
- Simplicity : With PrivateLink, you only need to manage your VPC and not the public aspects of your services, which simplifies network management.
- Compliance : For regulated industries with strict data handling requirements, PrivateLink helps maintain compliance by keeping traffic off the public internet.
How does it work ?
 [What is AWS
PrivateLink?](https://docs.aws.amazon.com/vpc/latest/privatelink/what-is-
privatelink.html)
[What is AWS
PrivateLink?](https://docs.aws.amazon.com/vpc/latest/privatelink/what-is-
privatelink.html)
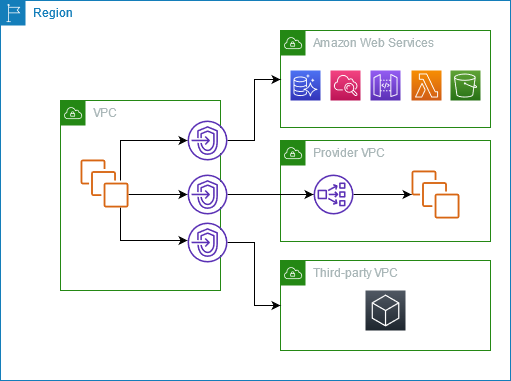
AWS PrivateLink components mainly include VPC service endpoints, endpoint services and network load balancers (NLBs).
Service endpoints are the PrivateLink-powered interfaces that live in your VPC, allowing you to connect to supported AWS services or your own services privately. These endpoints are highly resilient and scalable interfaces that provide a consistent network experience. Endpoint services, on the other hand, are the services you create or subscribe to that are accessible via PrivateLink. These can be AWS services such as S3, DynamoDB, or your own services, such as a Flask application, that you want to expose securely.
The Network Load Balancer plays an important role in the PrivateLink architecture. When you create an endpoint service, an NLB is used to distribute incoming traffic across multiple targets, such as EC2 instances, containers or IP addresses, in one or more availability zones. The NLB acts as a bridge between your VPC and the endpoint service, ensuring high availability and automatic scaling of incoming traffic.
 Simplified AWS
PrivateLink
Simplified AWS
PrivateLink
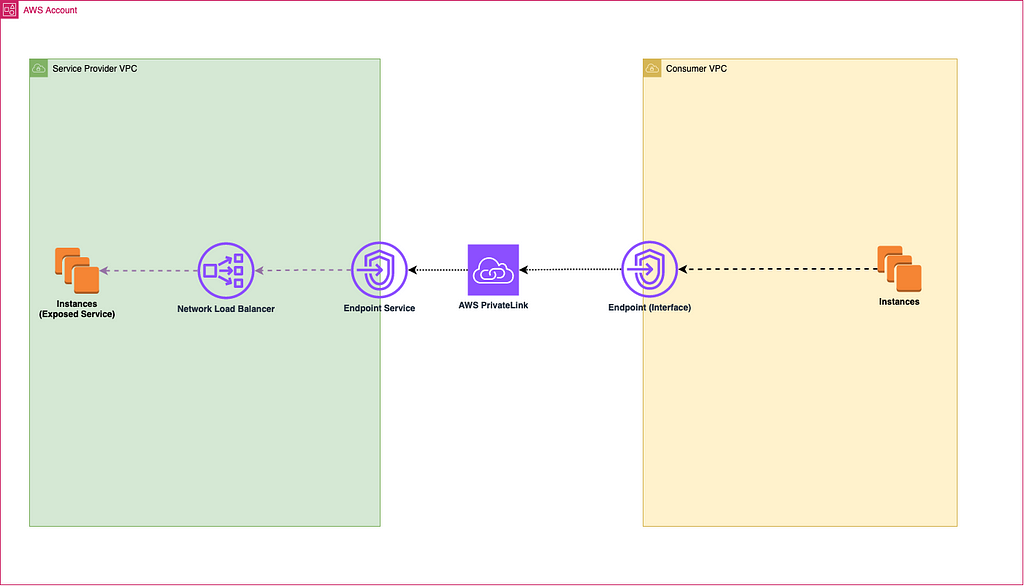
In a typical PrivateLink configuration, the owner of an AWS account creates an endpoint service and specifies the NLB to be associated with that service. Consumers of other VPCs can then connect to this service by creating an interface VPC endpoint (also known as an interface endpoint) in their own VPC. This interface endpoint acts as an elastic network interface (ENI) with private IP addresses that act as an entry point for traffic destined for the service.
PrivateLink securely routes traffic from the consumer’s VPC to the service by encapsulating it in the AWS network, without ever exposing it to the public internet. Network traffic is directed to the NLB via the interface endpoints, which then routes the traffic to the service.
[Service Provider] Expose a Flask application through PrivateLink
Step 1: Deploy a Flask Application
The Flask application we will be deploying is pretty simple :
First create a private EC2 instance with the following user data script that installs Python, Flask and deploys our application :
| |
When creating the EC2 instance, make sure to allow inbound traffic in port 5000 from the VPC CIDR.
Step 2: Configure Network Load Balancer (NLB)
Now create the NLB with a listener on port 5000 that forwards traffic to a Target Group where you register the EC2 instance created above as a target:
⚠️ If the targets are unhealthy, make sure you allow the traffic on port 5000 from the VPC CIDR in the EC2 Security group.
Add a listener on port 5000 and associate it with a target group
Step 3: Set Up an AWS PrivateLink Endpoint Service
Create the VPC Endpoint Service (Network) and choose the NLB from above:
Once created, copy the Service name (you will need it later) and allow the consumer principal (arn:aws:iam::378918992955:root which is same account in this case but it can be a different account):
[Service Consumer] Access the Flask application through PrivateLink
Step 1: Create a VPC Endpoint for the AWS PrivateLink Service
On service consumer side, create a VPC endpoint (interface endpoint) and specify the Service Name from the Endpoint Service above:
Once it’s created, it will remain inpending state until the Endpoint Service accepts the Endpoint connection (This is required sine acceptance required setting is enabled for the Endpoint Service):
The Endpoint Service should accept the connection:
⚠️ One last setting to do is to allow the traffic from the consumer VPC on port 5000 in the Network load balancer security group and do the same in the endpoint security group as well (allow resource within the consumer vpc to use the endpoint):
Step 2: Verifying Your AWS PrivateLink Setup
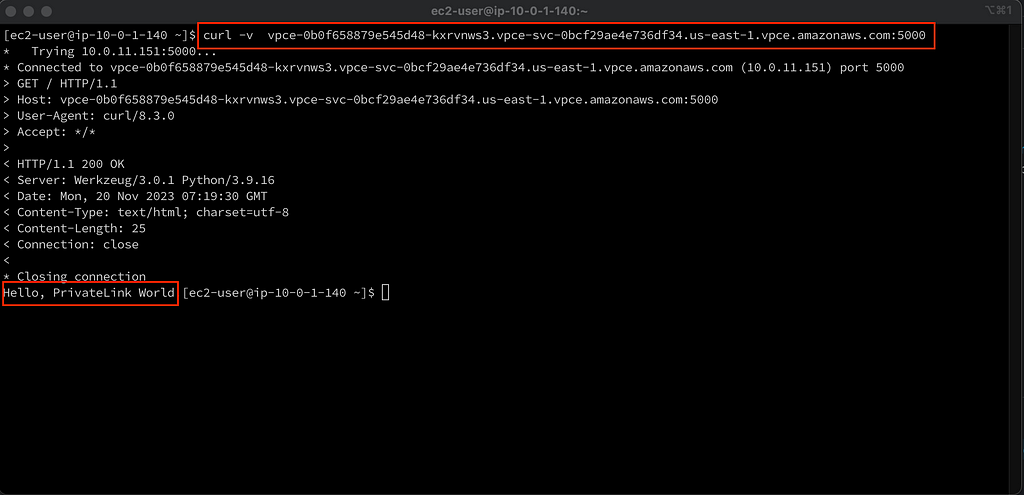
To test the setup,create a public EC2 instance that you can SSH into and see if you can access the Flask application through the PrivateLink Endpoint:
Testing the connection through the PrivateLink using the endpoint DNS Name and the Flask application port :
| |
Conclusion:
AWS PrivateLink is widely used by service providers to ensure direct and secure communication with customer accounts, minimising exposure to the public internet. Its ability to provide private connectivity has made it an indispensable feature for organisations that prioritise network security and efficiency.
I encourage you to take advantage of PrivateLink, as it offers a path to a more secure and controlled cloud environment. Experiment with its offerings and integrate it into your service architecture to discover its full potential for securing communications within the AWS ecosystem.
Read more:
AWS Inter-Region PrivateLink using Terraform
How Does AWS PrivateLink Works ? was originally published in AWS Morocco on Medium, where people are continuing the conversation by highlighting and responding to this story.
The content, views, and opinions expressed on this blog, awsmorocco.com, are solely those of the authors and contributors and not those of Amazon Web Services (AWS) or its affiliates. This blog is independent and not officially endorsed by, associated with, or sponsored by Amazon Web Services or any of its affiliates.
All trademarks, service marks, trade names, trade dress, product names, and logos appearing on the blog are the property of their respective owners, including in some instances Amazon.com, Inc. or its affiliates. Amazon Web Services®, AWS®, and any related logos are trademarks or registered trademarks of Amazon.com, Inc. or its affiliates.
awsmorocco.com aims to provide informative and insightful commentary, news, and updates about Amazon Web Services and related technologies, tailored for the Moroccan community. However, readers should be aware that this content is not a substitute for direct, professional advice from AWS or a certified AWS professional.
We make every effort to provide timely and accurate information but make no claims, promises, or guarantees about the accuracy, completeness, or adequacy of the information contained in or linked to from this blog.
For official information, please refer to the official Amazon Web Services website or contact AWS directly.

