Getting Started With OpenTofu (v1.7.0) on AWS — State Encryption.
- z4ck404
- Aws , Open TOFU , Terraform
- May 4, 2024
OpenTofu is a new open source tool for Infrastructure-as-Code (IaC) management across multiple cloud providers, created by the community following the terraform licence change by HashiCorp . With the recent v1.7.0 release , OpenTofu now supports state file encryption.
This guide explains how to configure OpenTofu to manage AWS resources with encrypted status files stored on a remote AWS S3 buckets backend using AWS Key Management Service (KMS).
1 — Why State Encryption:
State encryption is a very important security feature for infrastructure-as- code tools such as Terraform and OpenTofu. Initially, these tools stored the entire state file, including potentially sensitive access keys, passwords and resource details, in the clear in back-end storage such as S3 buckets or local files. This meant that anyone able to access the status file could see all the confidential data, creating a significant risk if the status file was compromised. Encrypting the contents of the status file protects this sensitive information from unauthorized access. Without encryption, infrastructure credentials and provisioning secrets could be exposed, allowing malicious individuals to make unwanted changes or gain access to private systems and data.
When you enable encryption, OpenTofu will encrypt state data at rest. If an attacker were to gain access to your state file, they should not be able to read it and use the sensitive values (e.g. access keys) contained in the state file. — OpenTofu docs
2 — Prerequisites
- An AWS account.
- The AWS CLI installed and configured.
- OpenTofu v1.7.0 installed (you can refer to OpenTofu docs to install or update Tofu CLI )
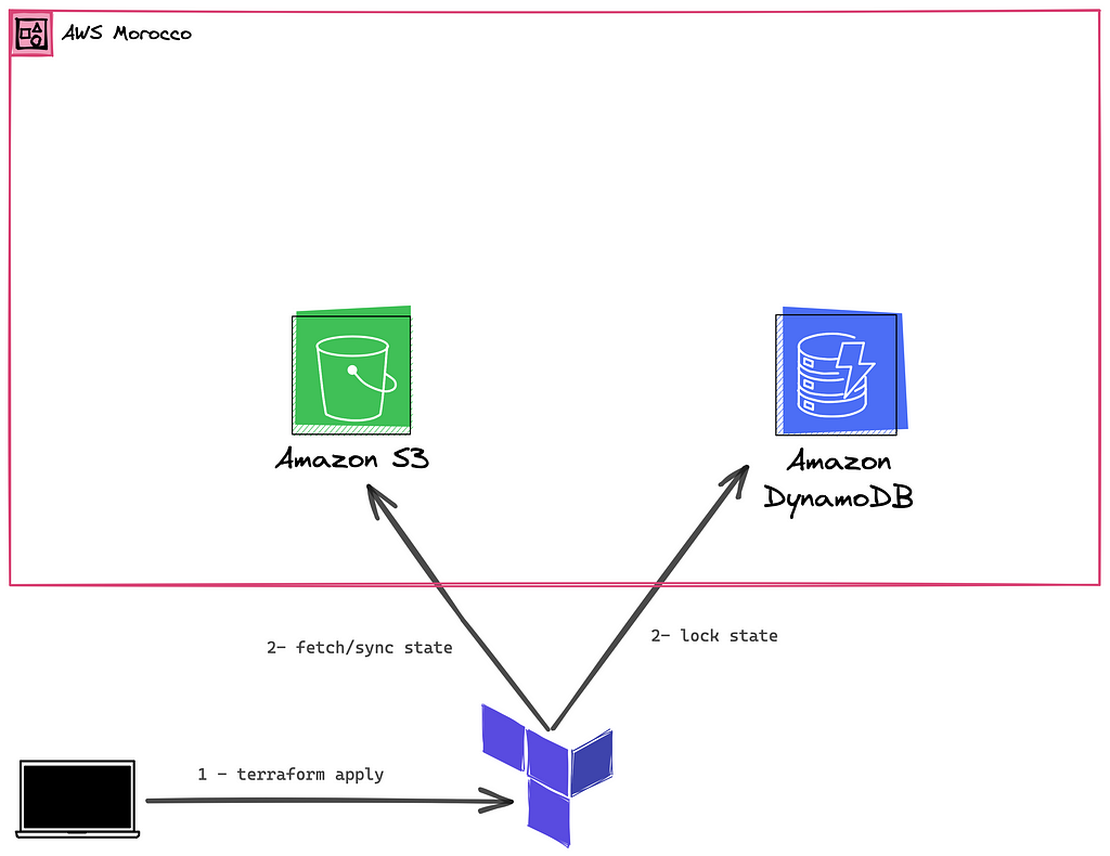
3 — OpenTofu s3 state backend:
In previous articles, we learned how to configure Terraform and start provisioning resources on AWS, and how to configure the s3 remote state backend with state locking on dynamoDB. The configuration is similar and valid for openTofu too, so you can refer to these articles to configure remote state if you haven’t already done so
- Getting Started With Terraform on AWS
- Getting Started With Terraform on AWS — State backend & State Locking
4— OpenTofu s3 state encryption:
First create the AWS key that you want to use to encrypt the state file
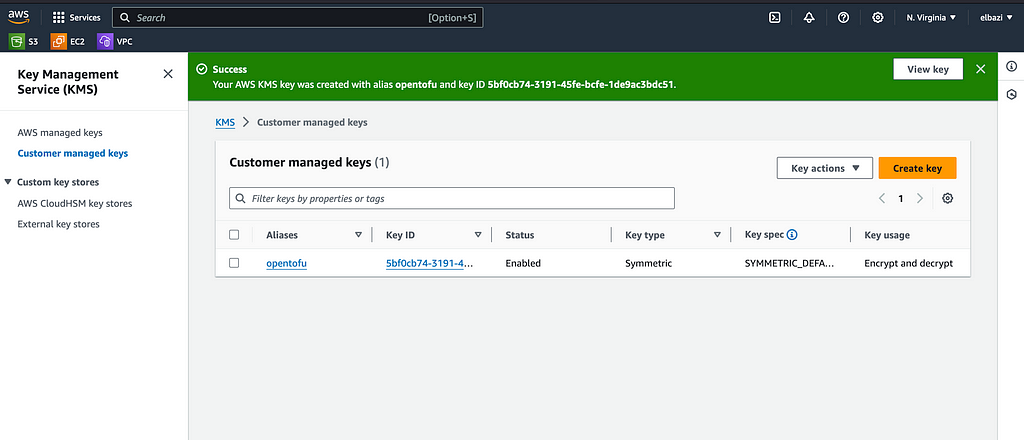
Then add the necessary
configs
in the
terraform{} section in the providers.tf file.
terraform {
encryption {
key_provider "aws_kms" "this" {
kms_key_id = "<kms-key-id>"
region = "us-east-1"
key_spec = "AES_256"
}
method "aes_gcm" "this" {
keys = key_provider.aws_kms.this
}
state {
method = method.aes_gcm.this
}
}
backend "s3" {
bucket = "awsmorocco-opentofu-states"
key = "awsmorcco/network"
dynamodb_table = "aws-morocco-opentofu-backend"
region = "us-east-1"
}
required_providers {
aws = {
source = "hashicorp/aws"
version = "5.21.0"
}
}
}
provider "aws" {
profile = "aws-admin"
alias = "prod"
}
If you add encryption to an existing Tofu project or you have already run tofu init before adding encryption , you need to migrate your unencrypted status file and encrypt it first.
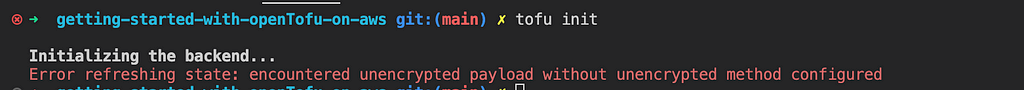
Tofu can handle this by adding a method to handle encrypted files (by default, it won’t even read the status file) and it will encrypt them the next time you apply (save the state file).
terraform {
encryption {
key_provider "aws_kms" "this" {
kms_key_id = "<kms-key-id>"
region = "us-east-1"
key_spec = "AES_256"
}
method "aes_gcm" "this" {
keys = key_provider.aws_kms.this
}
method "unencrypted" "migrate" {}
state {
method = method.aes_gcm.this
enforced = false
fallback {
method = method.unencrypted.migrate
}
}
}
with the following run main.tf :
resource "aws_vpc" "my_tofu_vpc_prod" {
cidr_block = "172.17.0.0/16"
tags = {
Name = "aws-morocco"
}
provider = aws.prod
}
After running opentofu apply, the new state file will be encrypted with the specified KMS key and uploaded to the S3 backend.
If you download and inspect the state file from S3, you’ll see that its contents are encrypted, protecting any sensitive data.
{
"serial": 3,
"lineage": "b437494d-2f15-27e5-ca7e-17ad12e9375c",
"meta": {
"key_provider.aws_kms.this": "eyJjaXBoZXJ0ZXh0X2Jsb2IiOiJBUUlEQUhqbU5HdTR2QzlGSkVxL2hrcmNuc0MwU0N1d29reTd2WTJwanRYY1VkaThQUUdKaVhSbGQ5cFJ1MlFhOUV1MU12amVBQUFBZmpCOEJna3Foa2lHOXcwQkJ3YWdiekJ0QWdFQU1HZ0dDU3FHU0liM0RRRUhBVEFlQmdsZ2hrZ0JaUU1FQVM0d0VRUU1kQ0RQZGdRdHd5dWpsUnBnQWdFUWdEdVVHVWpmOVI2TkJtQjhOcEIzUkZYdG15d3dnTlBQZDdHWklDREF1NFlYWEs3VElFN3VGOWVYRU5VRHEzNEdZRWloNFpBUW9BUVRXVDNaRnc9PSJ9"
},
"encrypted_data": "6nGVSqdSaz/7ck6YVn3L1acDM/wqIWy4eqUPBenak+9fJN+cSV/uq9L1hmZk9yJfMEymqws0/IaIU644bBMZ1GQVa1ujc++oPzr7nSGQRUc9kqTXiIlU3BPKw1SNzlcpV5LqNObVfiZ3BF0VQc0+Z7se3betkmRT4M+cNitYXTJ+AuLnqt2pNvYgRLLMB5+Tkc0jYByrOqtaO5AxaWgE1MAZUHlBlMqtGaW6G+xtnj8jRxBtHwefLQ/NuYl+oTvZ9SeMaFzn6xL9EBUyO+M4LesZcTmQyVTLYkucuBihCauWXsdneNxKj70NBaX+HK+ZzqUIu24Yn7MEVEOj9/K9Q2DvsujLQ2J0jmMvVC+Zp6U8My2XcZY3oLAN4nywzVLLHK0aQCUaWssZ5wyKDCwriP2/D2dzcTFSfFE75wbPqZexuKXv9sdTRNCAlDMPipmhfBNNIYCvPJFg2jUINXvesT/ghVRdApy3dZHakqwg2+SWkCc96Ul9Ok/Tm+OC6DiAHjZvUeJUJW7fsUbClsGnXgZhMIZEeL7LxqlysAD6ozdCjAQrfr0uuPcYrtn6Ib7IXm34zf91hzLlnyOf0VDVOz+NzrQsW7GSNKYRutUN6RwDU++jo+9nmwTOKN+0OWKZitAKt6+sGomNUHwI7CnaV54jJKK0VD3ZAS6epTQ4NpH68IVyV4ZBX9qCajosP75U+2Kf9A29adgEx3iAzkyJrx7xT9JWC/bcU89TFy88byivbI86aGS+SR+oMRxZT5prKvX7StB2igTJG/2RRt+XPLlt53G+XIbrLQPk2CBuVBdaoVJD1umeuzrpUQbhSRinN2WcJiKtvbVWGCE8BY4I/2aUFh059QKrXT93rgqtrdkzp8eGN33D7OH7nPe9qHeo2kjjrnWYxIZBSHzSqDi1kcY6rQV88j30bP+T3KBEE9l+skbiNMwVvgzNfbodOpkMiVgqOiPBXc1oIHCbutO1U1sLmdTFpvEXJwwm30Z9ZF6Rj5O7k5/B3e1LAtGFz9pHaD1KSsuGVWFcEG3pbu8ibxrCz1fK7ey4JotrKWG+O1xFhgUjeFpTxbhaVZqPnz7+OcGddtHAcqy7LbJZ9YsLXConrDagYBcwS6dpH11vBPCg98I5GBct3bl3uE3Ns/TfQGflZGuhKgyg2OqVIEKkFIPwbFMBSE+YnmzRmY1g0mroQDICMFQl7GYGu/D4GRaflyGBr4KFx8HYDPnpuEk0d2f0200olBqYtVa+xQ7Ig0SaA4k5BfM9InvYiVqUE0uGERWRJdly6qaWlL4s2MOCyOIOa3K210W+rPVkqEdk70XxrE9Nwl7QSzfCiaiTgjbK/OP6ry8saGFyQGePL/rZ/oJKcDtKTmmmTWSiE1fk2Mf4bCZkLSjw4PXZ2Hxh0x92IaDPUE3GAHnU61MvTeTHi66XbQavvlQcYeQW4jsZNz682fFz0Qmn+TjB3vl3WUVp5KJE3cbZmaYwd/DGkAYT9iMXrsVc0b6f/kBObfIzVLhpYFkgtNz04VsCkw9l0zAS1QpKbq7crMif5DDD5natTCc062EyyDHgwgipTM3HDlh5nE8l6dmyeYn5RR4NMF+/M16hrAkiVFEU5lhzwLqqrMevY7FjJQuYeQXjyVcuQrOqW5sMnhSADjSkRY0I6F13wTRuX+nAoPfZZMwxhlymIMOjoCiNOpAw7008alFpX85yWoCgbJx1jXAbOMjB8iHoCr/T9AMoZacy4HB7BLOrRtsrISvnYzmIby8A3oGF6becacE2V3xXpd39GGsLBr7SbwRgeF15VZoE5t4sBf6n6fyXdVL7c4QlZ7W5I5boJ81szM3QKI4fnS2LVexPxbsqcNU4/8YSnYJ5DtQ86hfExDWKny5l/nO1YXNhvlwTnW30xAUg+VzSzn6Fu9+DkIBUPVNGcio3Z0w3+7hSK5XoIRPmIAQ82J2vjKIdjoK8dSO273hP0a3aeCsRoDcVRB+05nZb1DeYQCWDf4VFZ9IZJgtyBs/9GJcAgvfoIyE6qFakLTVJhXl86yIvwcDqFPDHxR+PnXb1+VK/Y2WTN+CXErVn5DSUTW952DVPQanspJDq3Cot9VYIDWCnqtIp2qD9au3r1LW0Ldfm6r9ubSmh2ItLSuKDF7S86dh59PdcYvA7X36woPaOqKZEoCM1SWgOlMOa94O55m2jT4ZgjERgR8LVkDh21qiymcYFDR54jaJN2FeBk/XLLBHSMfM4LCMc4oGPmZIAdER/QO+6J0vZwpXuiXXpiqptHE8YU9pIHbrql3XGx7iLlK2Xiqzj4h3cd06F5sPXq8q0JZaUA+RgCxjZpRUxn2kx/mlQHtXnwYJPr0Y5LWr5ABuMT4FJrAAkVrHXPuMxS3NtTfo=",
"encryption_version": "v0"
}
5 — Conclusion:
State encryption is an essential security feature for infrastructure-as-code tools like OpenTofu, and one that was long-awaited in Terraform as well, as it protects sensitive data such as access keys and passwords from unauthorized access. By following the steps outlined in this guide, you can configure OpenTofu to encrypt state files stored in an AWS S3 bucket using the AWS Key Management Service (KMS).
OpenTofu also offers customization options for encryption, allowing you to use other encryption key providers like GCP KMS, OpenBao, and more, providing flexibility to align with your organization’s security requirements.
Getting Started With OpenTofu (v1.7.0) on AWS — State Encryption. was originally published in AWS Morocco on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer for Awsmorocco.com
The content, views, and opinions expressed on this blog, awsmorocco.com, are solely those of the authors and contributors and not those of Amazon Web Services (AWS) or its affiliates. This blog is independent and not officially endorsed by, associated with, or sponsored by Amazon Web Services or any of its affiliates.
All trademarks, service marks, trade names, trade dress, product names, and logos appearing on the blog are the property of their respective owners, including in some instances Amazon.com, Inc. or its affiliates. Amazon Web Services®, AWS®, and any related logos are trademarks or registered trademarks of Amazon.com, Inc. or its affiliates.
awsmorocco.com aims to provide informative and insightful commentary, news, and updates about Amazon Web Services and related technologies, tailored for the Moroccan community. However, readers should be aware that this content is not a substitute for direct, professional advice from AWS or a certified AWS professional.
We make every effort to provide timely and accurate information but make no claims, promises, or guarantees about the accuracy, completeness, or adequacy of the information contained in or linked to from this blog.
For official information, please refer to the official Amazon Web Services website or contact AWS directly.