EKS Pod Identity or IAM Roles for Service Accounts (IRSA) ?
 Photo by Isfak
Himu
on Unsplash
Photo by Isfak
Himu
on Unsplash
Managing secure access to AWS resources has always been a major concern in EKS and a headache for cluster administrators. IRSAs (IAM Roles for Service Accounts), which we’ve covered in detail in this article, have been very useful in facilitating this process since their introduction in 2019, but had many limitations and required significant configuration and maintenance effort.
Then, AWS introduced EKS Pod Identity at the end of2023, which was a major step forward in simplifying and improving this process. This article looks at what EKS Pod Identity is, how it works and why it’s a game-changer for Kubernetes developers and administrators.
What is Amazon EKS Pod Identity?
Amazon EKS Pod Identity is a new feature that further simplifies the way cluster administrators configure Kubernetes applications to get AWS IAM permissions. It builds on the foundations established by IRSA, but offers a more streamlined approach.
Key aspects of EKS Pod Identity include:
- Simplified Configuration : Permissions can now be easily configured with fewer steps directly through the EKS console, APIs, and CLI.
- No OIDC Requirement : Unlike IRSA, EKS Pod Identity doesn’t require setting up an OpenID Connect (OIDC) provider for each cluster.
- Direct Role-to-Service Account Mapping : EKS Pod Identity allows mapping of IAM roles to service accounts directly in the Amazon EKS console, APIs, or AWS CLI.
- Cross-Cluster Role Usage : It’s easy to use an IAM role across multiple clusters without updating the role trust policy for each new cluster.
- Pod Identity Agent : EKS Pod Identity introduces a new component called the Pod Identity Agent that runs as a DaemonSet in the cluster.
- Role Session Tags : Supports role session tags with attributes such as cluster name, namespace, and service account name.
How Does EKS Pod Identity Work?
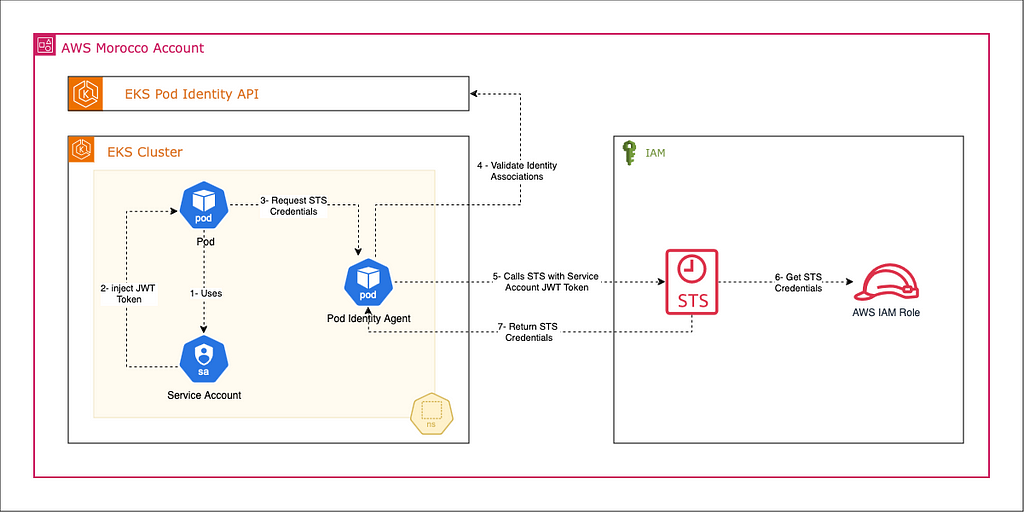
The EKS Pod Identity process can be split into the following steps:
- A pod (the application’s AWS SDK/CLI) requests credentials from the EKS Pod Identity Agent.
- The pod identity agent calls the Auth EKS AssumeRoleForPodIdentity API, which validates the identity association.
- After validation, the EKS Auth API calls STS to provide temporary AWS credentials, which it sends back to the pod identity agent.
- The identity agent passes these credentials to the pod.
- The pod can now use these temporary credentials to access AWS resources.
This process ensures secure, ephemeral access to AWS resources without the headaches of managing long-term credentials.
Benefits of EKS Pod Identity
- Simplified Workflow : Cluster administrators no longer need to switch between Amazon EKS and IAM services to authenticate applications to AWS resources.
- Reduced Configuration Overhead : Eliminates the need for OIDC provider setup and trust policy updates for each new cluster.
- Improved Scalability : Easier to manage permissions across multiple clusters and namespaces.
- Enhanced Security : Maintains the principle of least privilege while simplifying the implementation process.
- Kubernetes-Native Management : Allows for more centralized and Kubernetes-native management of IAM role associations.
How To Setup EKS Pod Identity ?
The process of implementing EKS Pod Identity can be broken down into three simple steps:
0 — Prerequisites:
- The cluster verison must be ≥ 1.24 (refer to this doc for more details)
- The identity Agent Daemon works only on the worker nodes that are Linux Amazon EC2 instances.
- The applicatin should use the latest AWS SDKs (refer to this doc for more details )
- The EC2 node must have the permissions for the agent to do AssumeRoleForPodIdentity action in the EKS Auth API.
1 — Create an IAM Role :
Create an IAM role with the required permissions for your application and specify pods.eks.amazonaws.com as the service principal in its trust policy.
2 — Install the EKS Pod Identity Agent :
Install the Amazon EKS Pod Identity Agent add-on using the Amazon EKS console or AWS Command Line Interface (AWS CLI).
 Amazon EKS console — Add-ons tab
Amazon EKS console — Add-ons tab
| |
3 — Map the Role to a Service Account :
Map the IAM role to a Kubernetes service account directly in the Amazon EKS console, APIs, or AWS CLI.
Using Terraform
You can also use terraform to manage these association with Iac using this module from terraform-aws-modules .
Once these steps are completed, any new pods that use the associated service account will automatically be configured to receive IAM credentials.
Migrating from IRSA to EKS Pod Identity
For those already using IRSA, migration to EKS Pod Identity is straightforward:
- Upgrade your EKS cluster to version 1.24 or later.
- Install the EKS Pod Identity Agent Add-on.
- Update your applications to use supported AWS SDK versions.
- Modify your IAM roles’ trust policies to include the new EKS service principal.
- Create EKS Pod Identity associations using the new API.
Conclusion
Amazon EKS Pod Identity represents a significant improvement in IAM authorization management for Kubernetes workloads on AWS. It simplifies configuration and improves scalability and security compared to IRSA. EKS Pod Identity is recommended if you meet the prerequisites for a more streamlined, secure and scalable approach to IAM authorization management. And for those who can’t meet the conditions yet, and are waiting for future updates, IRSA remains a viable alternative.
ℹ️Architecture diagram in raw format is available here : aws-morocco-samples/aws-eks-pod-identity/materials at main · Z4ck404/aws-morocco-samples
EKS Pod Identity or IAM Roles for Service Accounts (IRSA)? was originally published in AWS Morocco on Medium, where people are continuing theconversation by highlighting and responding to this story.