Container Storage Interface (CSI) drivers play a crucial role in managing persistent storage for containerized applications. When working with Amazon Elastic Kubernetes Service (EKS), integrating CSI drivers becomes essential for efficient storage management. In this guide, we will delve into the details of CSI drivers on Amazon EKS and explore how to install and use them seamlessly with file systems.
Understanding CSI Drivers:
CSI is a standardized interface that allows storage vendors to develop plugins that can be used across various container orchestration platforms. With EKS, these drivers help manage the lifecycle of storage resources, enabling dynamic provisioning, attaching, and detaching volumes to and from pods
AWS EBS CSI Driver:
1 — Overview: The AWS EBS CSI Driver allows Kubernetes clusters to use Amazon Elastic Block Store (EBS) volumes as persistent storage. It supports dynamic provisioning of EBS volumes, attaching/detaching volumes to pods, and snapshot creation.
2 — Installation:
First Ensure that the necessary IAM roles and policies are in place to allow EKS to interact with the storage service. This involves creating a role with the appropriate permissions for your chosen driver as detailed in the AWS Docs.
To Deploy the EBS CSI Driver Utilize the provided Helm charts or YAML manifests to deploy the CSI driver on your EKS cluster or You can install it as an EKS Add-on and specify the IAM role you.
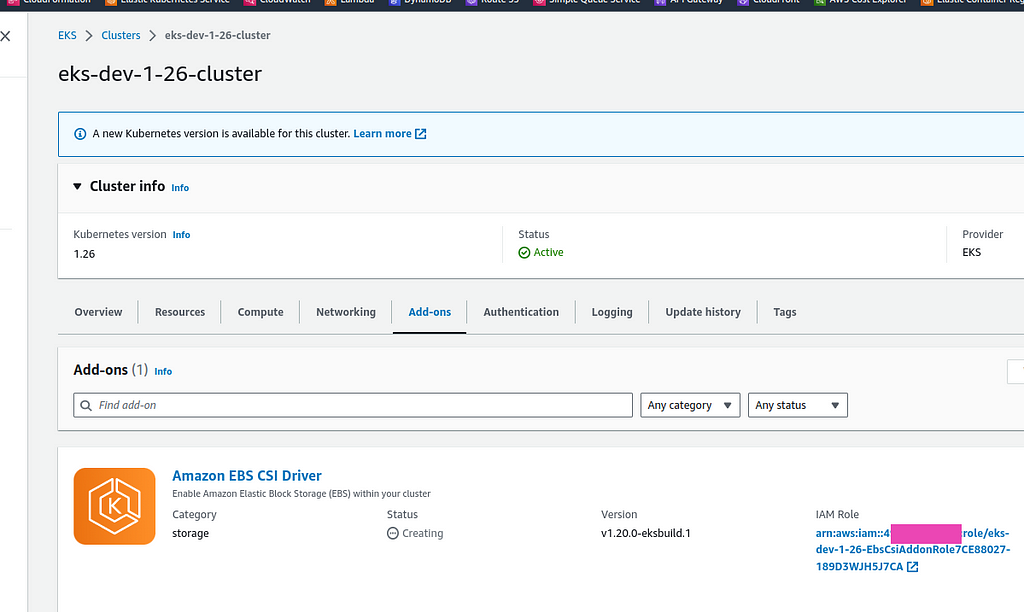 EBS CSI Driver add-on
EBS CSI Driver add-on
Or you can use my Terraform Module to setup the appropriate policy, and roles and install the add-on on the cluster.
[GitHub - Z4ck404/terraform-aws-eks-ebs-csi-driver: A terraform module install ebs csi driver on an eks cluster](https://github.com/Z4ck404/terraform-aws- eks-ebs-csi-driver)
3 — Usage:
Create a storage class that provisions volumes using the EBS driver, then define a PVC to be used by your workloads.
| |
Amazon EFS CSI Driver
1 — Overview:
Enables the use of Amazon Elastic File System (EFS) as a persistent storage solution for Kubernetes pods. It allows Dynamic provisioning of EFS filesystems, mount targets per pod, and support for ReadWriteMany access mode.
2 — Installation: Same as the EBS CSI Driver you will need to setup IAM resources, then install the driver using helm charts, yaml manifests, or as an EKS Add-on as explained in the AWS Docs.
3 — Usage:
Create a storage class that provisions volumes using the efs driver, then define a PVC to be used by your workloads.
| |
S3 CSI Driver (mounting S3 as a filesystem):
1 — Overview: The S3 CSI Driver allows Kubernetes pods to use Amazon S3 buckets as if they were mounted file systems. It enables transparent access to S3 data, and supports for ReadWriteOnce access mode.
2 — Installation:
Same as the EBS CSI Driver you will need to setup IAM resources, then install the driver using helm charts, yaml manifests or as an EKS Add-on as explained in the AWS Docs.
Or you can use my Terraform Module to setup the appropriate policy, and role and install the add-on on your cluster.
3 — Usage:
You can have a look into the examples in the official repository of the mountpoint-s3-csi-driver. Static provisioning can be achieved as follows:
| |
Conclusion:
These examples offer a basis for integrating and using different CSI drivers on Amazon EKS, addressing different storage needs, from block storage with EBS to file storage with EFS and even object storage with S3. There is also an Amazon FSx for Lustre CSI driver for FSx for Lustre. Third-party CSI drivers exist to support other file systems available on AWS such as NetApp Trident which allow FSxONTAPto be used.
CSI Drivers (EBS, EFS, S3) on EKS And How To Use Them was originally published in AWS Morocco on Medium, where people are continuing the conversation by highlighting and responding to this story.
The content, views, and opinions expressed on this blog, awsmorocco.com, are solely those of the authors and contributors and not those of Amazon Web Services (AWS) or its affiliates. This blog is independent and not officially endorsed by, associated with, or sponsored by Amazon Web Services or any of its affiliates.
All trademarks, service marks, trade names, trade dress, product names, and logos appearing on the blog are the property of their respective owners, including in some instances Amazon.com, Inc. or its affiliates. Amazon Web Services®, AWS®, and any related logos are trademarks or registered trademarks of Amazon.com, Inc. or its affiliates.
awsmorocco.com aims to provide informative and insightful commentary, news, and updates about Amazon Web Services and related technologies, tailored for the Moroccan community. However, readers should be aware that this content is not a substitute for direct, professional advice from AWS or a certified AWS professional.
We make every effort to provide timely and accurate information but make no claims, promises, or guarantees about the accuracy, completeness, or adequacy of the information contained in or linked to from this blog.
For official information, please refer to the official Amazon Web Services website or contact AWS directly.
