In the world of AWS networking, securing and optimizing communication between your VPC resources and AWS services is crucial. This is where AWS VPC Endpoints come into play — a feature that allows you to privately connect your VPC to supported AWS services without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect. This article explains what VPC Endpoints are, their types, their purpose, and how to configure them in your AWS environment.
Understanding AWS VPC Endpoints
Traditionally, to access AWS services from resources within a VPC, you would need to route traffic through the public internet. This approach has several limitations:
1. It exposes your traffic to potential security risks. 2. It can lead to higher data transfer costs. 3. It may introduce latency in your applications.
VPC Endpoints solve these problems by providing a secure and efficient way to access AWS services directly from your VPC. This means:
- You can keep your traffic within the AWS network, enhancing security.
- You can reduce data transfer costs by avoiding internet-bound traffic.
- You can improve network performance with reduced latency.
Types of VPC Endpoints
AWS offers three types of VPC endpoints:
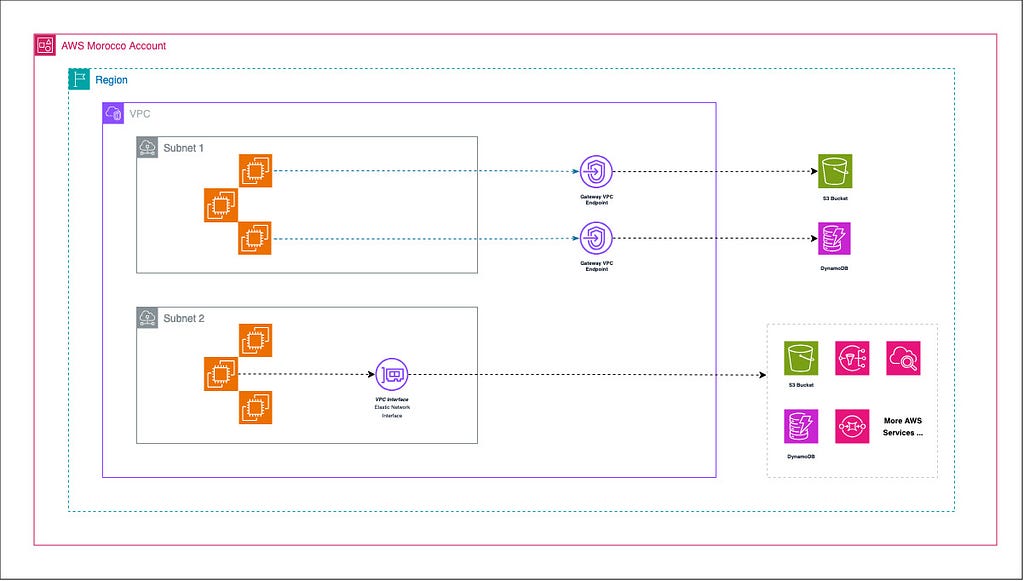
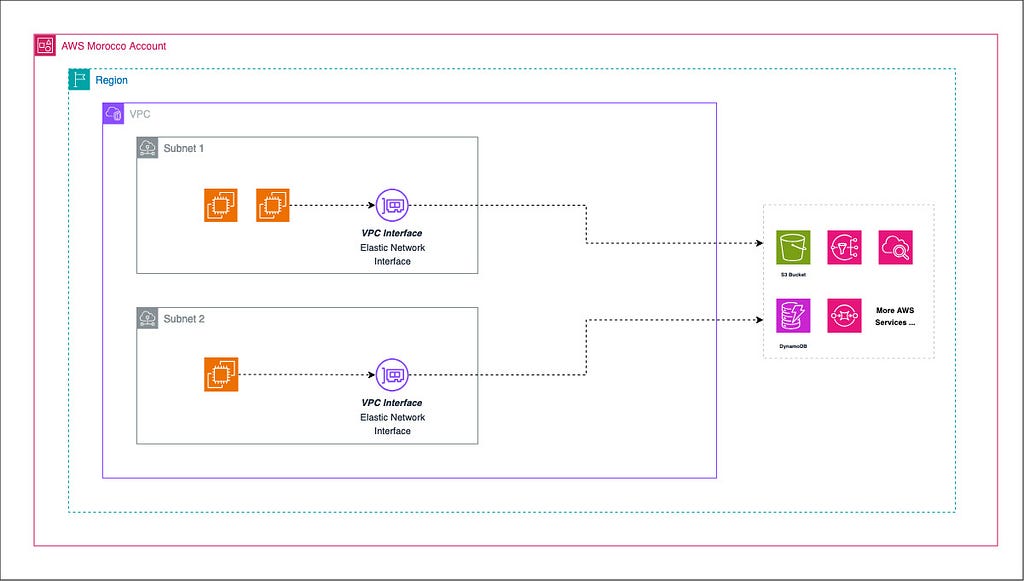
1 — Interface Endpoints : These endpoints provide private connectivity to services powered by AWS PrivateLink (For more details on this, refer to this article). They are essentially elastic network interfaces (ENIs) with private IP addresses in your VPC.
 Interface VPC
Endpoints
Interface VPC
Endpoints
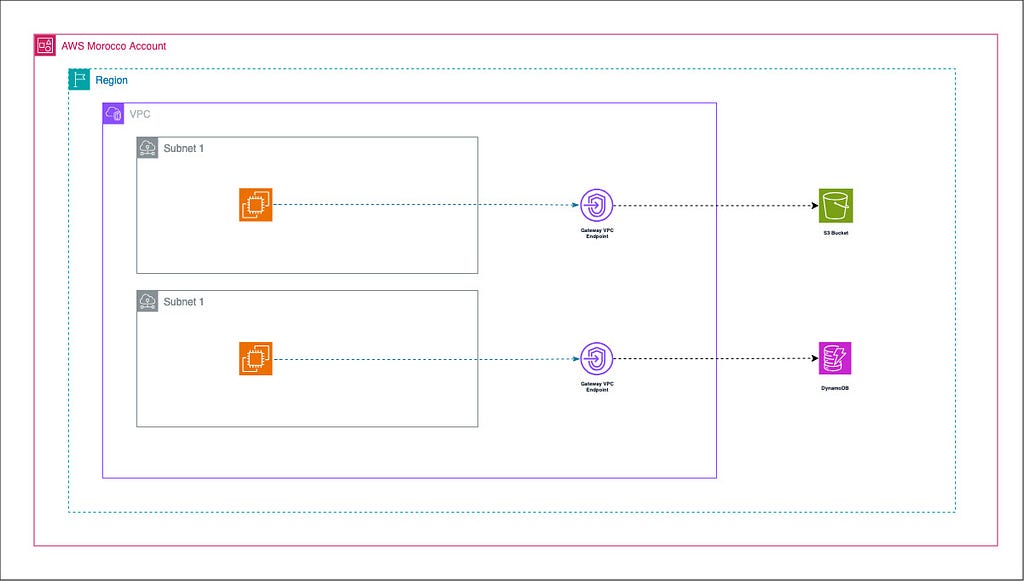
2 — Gateway Endpoints : These are gateways that you specify as a target for a route in your route table for traffic destined to supported AWS services. Currently, gateway endpoints are available for Amazon S3 and DynamoDB.
 Gateway VPC Endpoints
Gateway VPC Endpoints
Purpose of VPC Endpoints
The primary purposes of VPC Endpoints are:
1. Enhanced Security : By keeping your traffic within the AWS network, you reduce exposure to potential threats on the public internet.
2. Improved Performance : Direct connectivity to AWS services can lead to lower latency and higher throughput.
3. Cost Reduction : By avoiding data transfer over the internet, you can reduce your data transfer costs.
4. Simplified Network Architecture : VPC Endpoints can eliminate the need for internet gateways, NAT devices, or firewall proxies in many use cases.
5. Compliance : For applications that have strict data privacy requirements, VPC Endpoints ensure that traffic to AWS services doesn’t traverse the public internet.
How VPC Endpoints Work
Gateway Endpoints (for S3 and DynamoDB):
- You create a Gateway Endpoint for S3 or DynamoDB in your VPC.
- AWS adds a route to your specified route tables, with the service prefix as the destination and the endpoint ID as the target.
- When a resource in your VPC needs to access S3 or DynamoDB, it sends the request using the service’s public DNS name.
- Your VPC route table directs this traffic to the Gateway Endpoint.
- The Gateway Endpoint routes the traffic directly to the AWS service within the AWS network.
- The AWS service processes the request and sends the response back through the Gateway Endpoint.
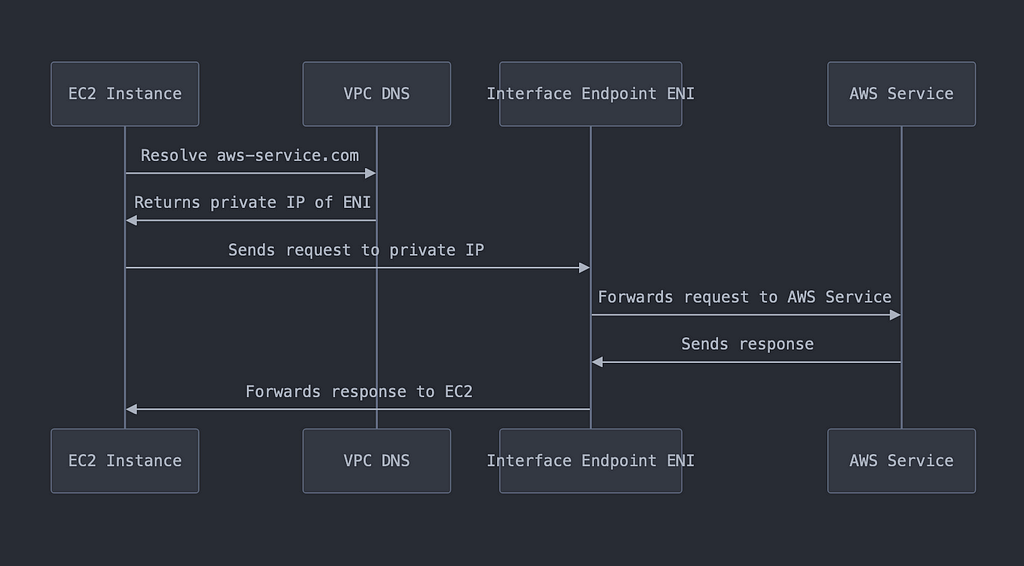
Interface Endpoints (for other AWS services):
- You create an Interface Endpoint for an AWS service in your VPC.
- AWS creates an Elastic Network Interface (ENI) with a private IP address in your specified subnet(s).
- AWS also creates new DNS entries that resolve the service’s domain to the private IP of the ENI.
- When a resource in your VPC needs to access the AWS service, it sends the request using either the service’s public DNS name or the endpoint-specific DNS name.
- DNS resolution within your VPC directs this request to the private IP of the Interface Endpoint ENI.
- The Interface Endpoint forwards the traffic directly to the AWS service within the AWS network.
- The AWS service processes the request and sends the response back through the Interface Endpoint.
 How VPC Interface
Endpoints Work
How VPC Interface
Endpoints Work
In both cases, your VPC resources can access AWS services without the traffic ever leaving the Amazon network, enhancing security and potentially improving performance.
Setting Up VPC Endpoints
The setup process differs for Gateway and Interface Endpoints. Let’s go through the steps for each:
Setting Up a Gateway Endpoint (e.g., for Amazon S3)
1 — Open the Amazon VPC console, Navigate to Endpoints and click “Create Endpoint”
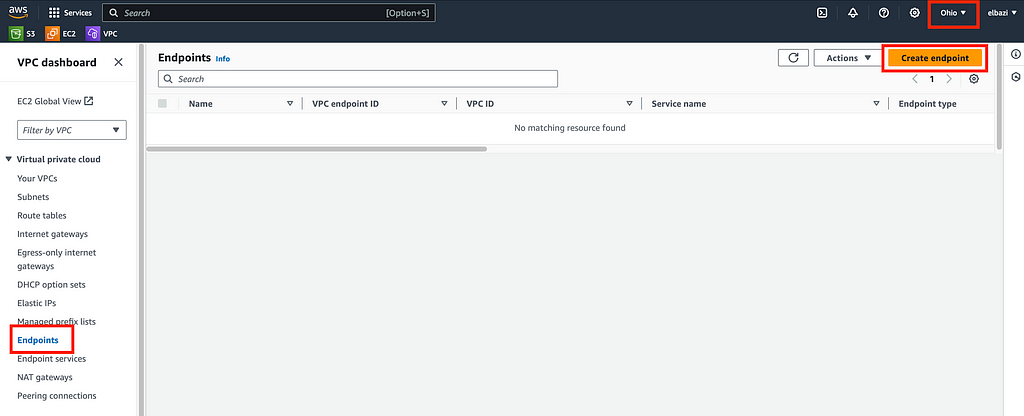
2 — Select the service: Choose “com.amazonaws.[region].s3” from the list of AWS services
3— Select the VPC where you want to create the endpoint
4 — Configure route tables: Select the route tables that should use the endpoint. AWS will add a route to these tables
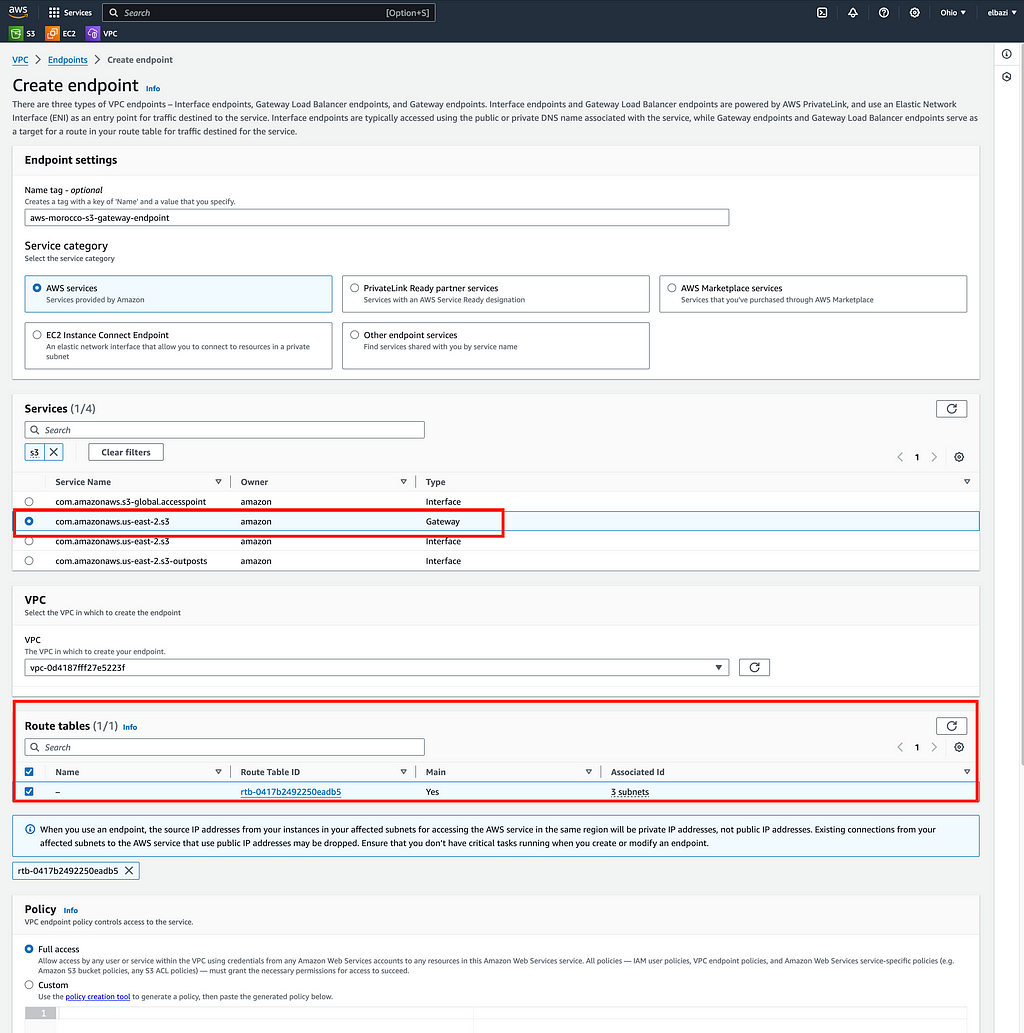
5 — Review and create: Review your settings and click “Create endpoint”
Here’s how you might do this using the AWS CLI
Setting Up an Interface Endpoint (e.g., for Amazon SQS)
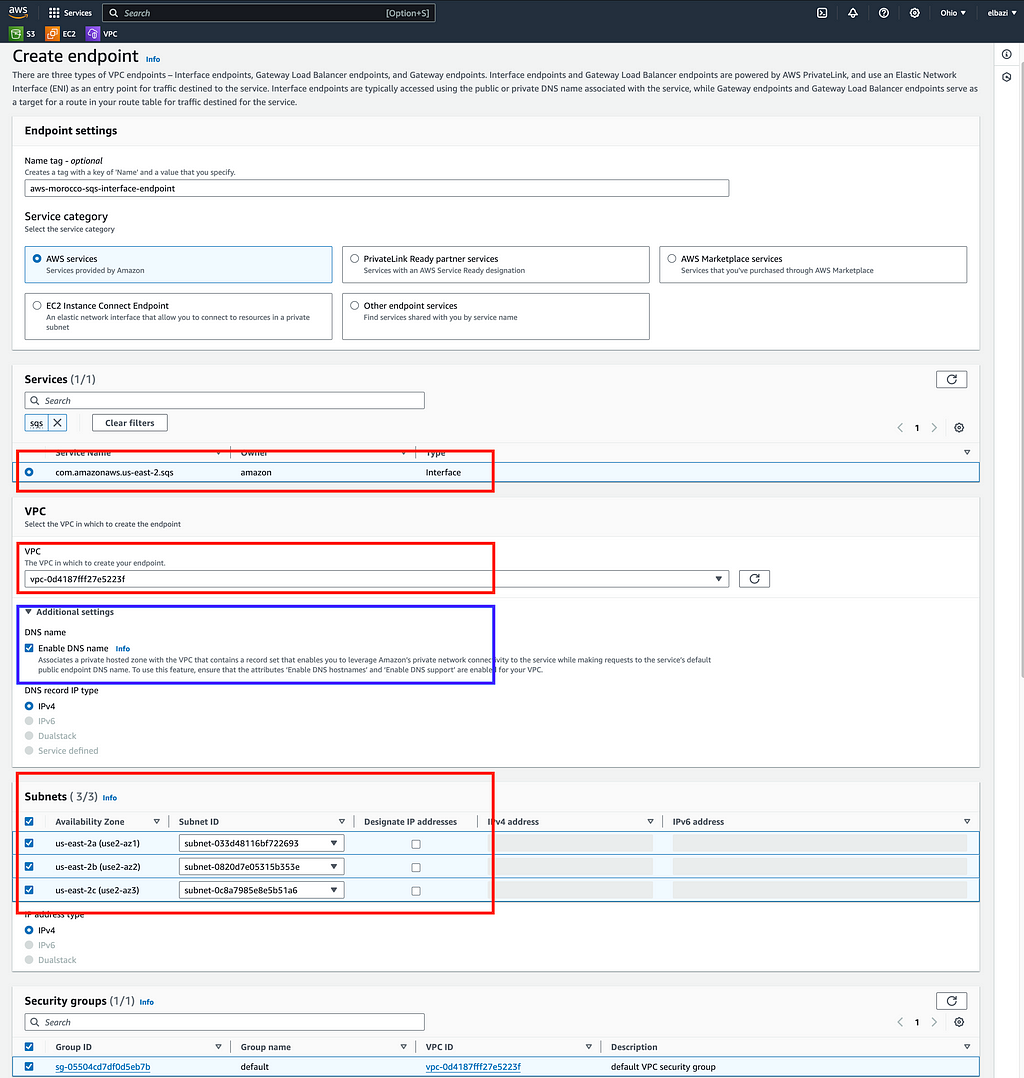
1 — Open the Amazon VPC console, Navigate to Endpoints and click “Create Endpoint”
2 — Select the service: Choose com.amazonaws.[region].sqs from the list of
AWS services
3 — Select the VPC where you want to create the endpoint
4 — Select subnets: Choose the subnets where you want AWS to create the endpoint network interfaces
5 — Configure security groups: Select the security groups to associate with the endpoint network interfaces
6 — (Optional) Enable private DNS: This allows you to use the default DNS name for the service
7 — Review and create: Review your settings and click “Create endpoint”
Here’s how you might do this using the AWS CLI:
Verifying the Setup
To verify that your VPC Endpoint is working correctly:
1. Check your route table. You should see a new route for S3 traffic pointing to the VPC Endpoint.
2. Try accessing S3 from an EC2 instance in your VPC. The traffic should now go through the VPC Endpoint.
| |
3. You can also use VPC Flow Logs to verify that your S3 traffic is no longer going through your internet gateway.
Best Practices
1. Use VPC Endpoints wherever possible to keep your AWS service traffic within the AWS network.
2. For services that support both Interface and Gateway Endpoints (like S3), prefer Gateway Endpoints as they are free and don’t count against your ENI limits.
3. Use VPC Endpoint policies to further restrict access to AWS services.
4. Monitor your VPC Endpoint usage with CloudWatch metrics to ensure they’re meeting your performance needs.
Conclusion
VPC Endpoints are a powerful tool in your AWS networking toolkit. By providing secure, efficient access to AWS services, they can significantly enhance the security and performance of your AWS infrastructure.
ℹ️ Architecture diagram in raw format is available here
- aws-morocco-samples/aws-vpc-endpoints/materials at main · Z4ck404/aws-morocco-samples
- What are VPC endpoints?
AWS VPC Endpoints: Balancing Security, Performance, andCost was originally published in AWS Morocco on Medium, where people are continuing the conversation by highlighting and responding to this story.
The content, views, and opinions expressed on this blog, awsmorocco.com, are solely those of the authors and contributors and not those of Amazon Web Services (AWS) or its affiliates. This blog is independent and not officially endorsed by, associated with, or sponsored by Amazon Web Services or any of its affiliates.
All trademarks, service marks, trade names, trade dress, product names, and logos appearing on the blog are the property of their respective owners, including in some instances Amazon.com, Inc. or its affiliates. Amazon Web Services®, AWS®, and any related logos are trademarks or registered trademarks of Amazon.com, Inc. or its affiliates.
awsmorocco.com aims to provide informative and insightful commentary, news, and updates about Amazon Web Services and related technologies, tailored for the Moroccan community. However, readers should be aware that this content is not a substitute for direct, professional advice from AWS or a certified AWS professional.
We make every effort to provide timely and accurate information but make no claims, promises, or guarantees about the accuracy, completeness, or adequacy of the information contained in or linked to from this blog.
For official information, please refer to the official Amazon Web Services website or contact AWS directly.