AWS EKS Required Add-Ons: A Comprehensive Guide
- z4ck404
- Aws , Eks , Kubernetes
- August 11, 2024
Table of Contents
Amazon Elastic Kubernetes Service (EKS) is a managed Kubernetes service that simplifies the process of deploying, managing, and scaling containerized applications. To ensure optimal functionality and performance, EKS relies on several essential add-ons.
In this article, we’ll explore three crucial EKS add-ons: AWS VPC CNI , Kube-proxy , and CoreDNS. We’ll delve into what they are, how they work, why they’re indispensable for your EKS cluster, and when they became required components.
The Shift to Required Add-Ons
Before we dive into each add-on, it’s important to understand why these components became required for EKS. In Kubernetes version 1.21, the Kubernetes community began the process of removing in-tree cloud provider code. This decision was made to improve the maintainability of Kubernetes and to allow cloud providers to develop and update their integrations independently of the Kubernetes release cycle.
As a result, functionality that was previously built into Kubernetes needed to be replaced by external components. For EKS, this meant that certain add-ons became required to maintain full functionality. AWS began this transition in 2022, with the process continuing through 2023 and beyond.
AWS VPC CNI:
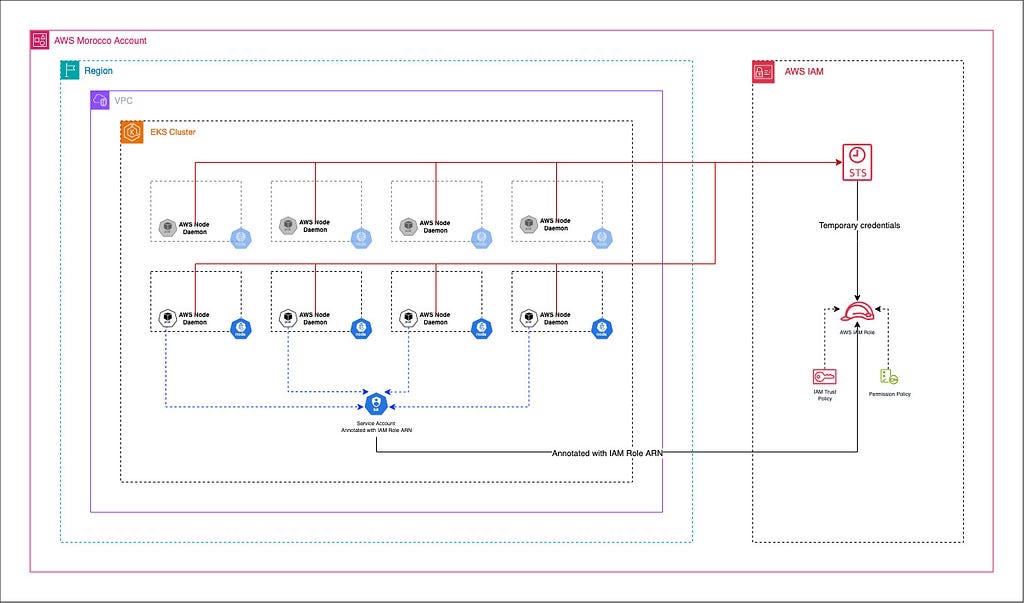 How does VPC CNI works
How does VPC CNI works
The AWS VPC CNI is a networking plugin for Kubernetes that allows Kubernetes pods to have the same IP address inside the pod as they do on the VPC network.
How does it work?
1. IP Address Management : When a pod is scheduled, the CNI plugin
allocates an IP address from the VPC’s IP address pool and assigns it to the
pod.
2. Network Interface Creation : It creates and attaches an elastic
network interface (ENI) to the EC2 instance if needed to support the pod’s
networking requirements.
3. Route Configuration : The plugin configures routes on the host to
direct traffic to the correct pods.
4. Pod Networking : It sets up the necessary networking within the pod,
including creating virtual ethernet (veth) pairs and configuring namespaces.
It requires an IRSA IAM role for it to function properly (refer to this guide for more details)
How to install it ?
- Make sure you have an AWS Identity and Access Management (IAM) OpenID Connect (OIDC) provider for your cluster (Refer to this guide to determine whether you already have one, or to create one, see Create an IAM OIDC provider for your cluster )
- Create an IAM role with the AmazonEKS_CNI_Policy IAM policy (use the IPv6 policy if your cluster uses the IPv6 family) attached to it. (Refer to this guide for more information)
Why is it important?
- Enables native VPC networking for pods
- Provides better performance compared to overlay networks
- Allows for easier integration with other AWS services
- Supports security groups at the pod level
When did it become required?
The AWS VPC CNI has been a critical component of EKS since its launch. However, it became an official required add-on as part of AWS’s response to the removal of in-tree cloud provider code in Kubernetes.
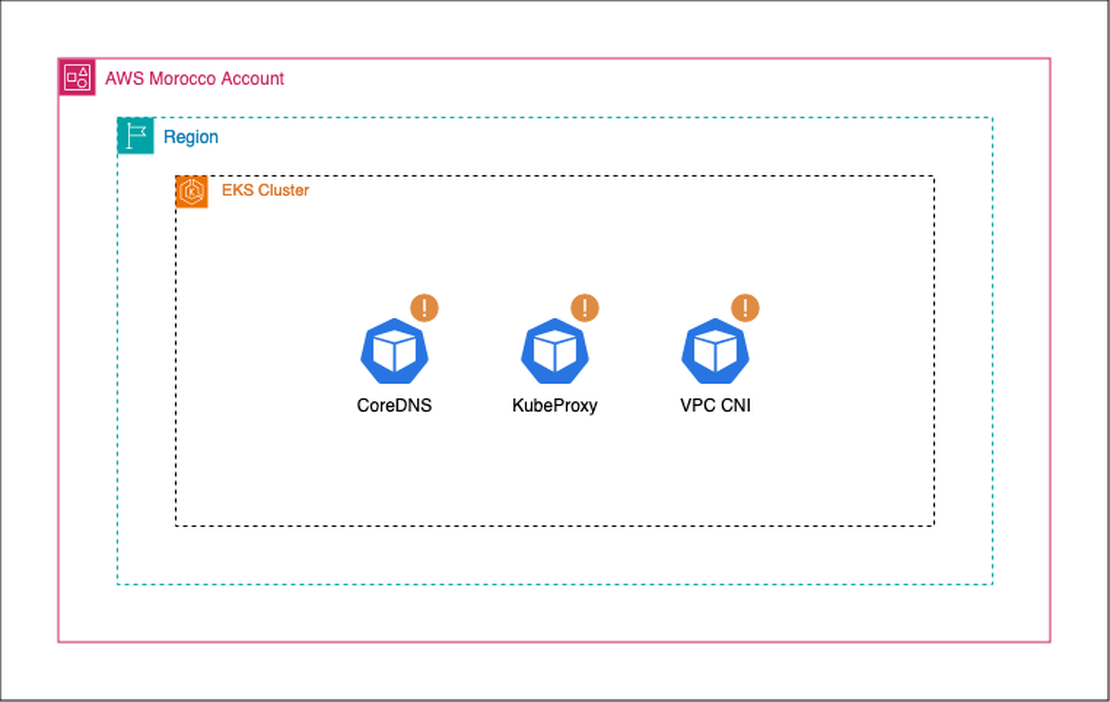
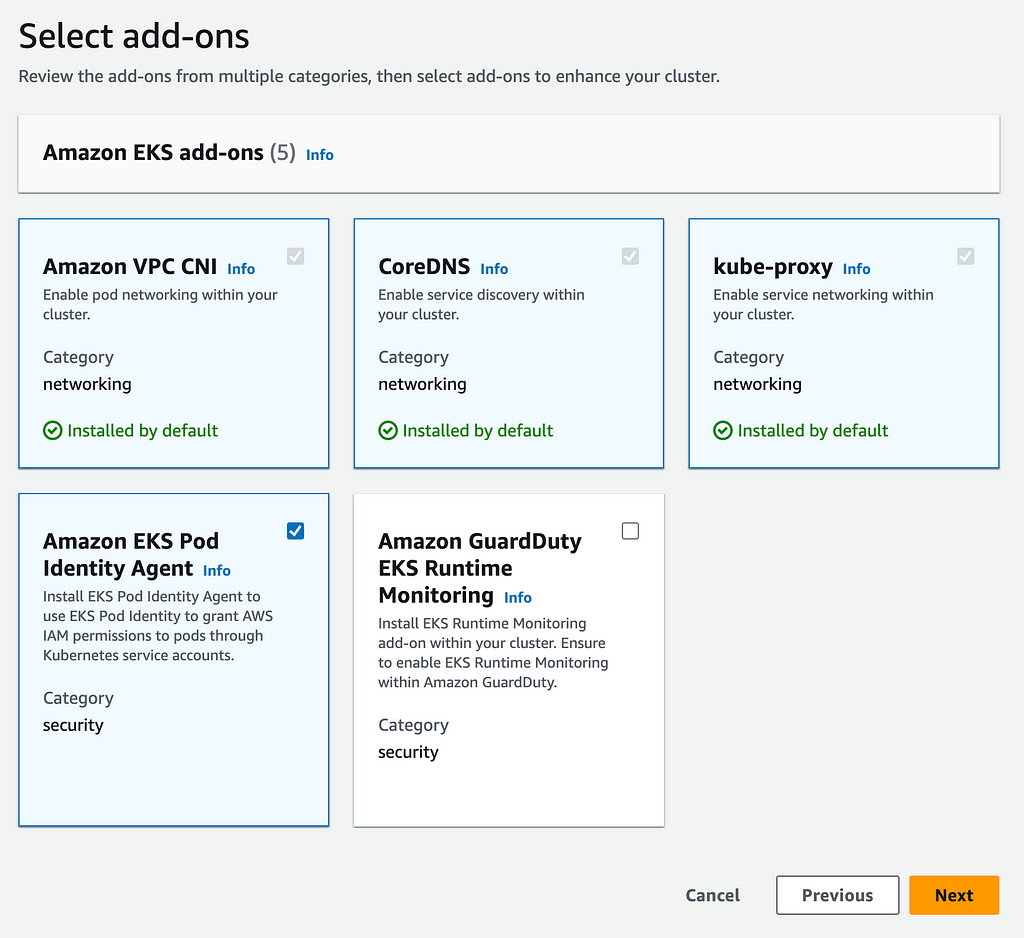 AWS EKS Add-ons
AWS EKS Add-ons
Kube proxy:
Kube-proxy is a network proxy that runs on each node in the Kubernetes cluster. It’s responsible for maintaining network rules that allow communication to and from pods.
1 — How does it work?
1. Service Discovery : Kube-proxy watches the Kubernetes API server for
changes to Service and Endpoint objects.
2. iptables Rules : Based on these changes, it updates iptables rules on
each node to route traffic to the appropriate pods.
3. Load Balancing : For services with multiple pods, kube-proxy
implements simple round-robin load balancing.
4. NodePort and LoadBalancer Services : It manages the necessary rules
for these service types, allowing external access to services.
2 — How to install it ?
It should be installed on a newly created EKS cluster and if not you can either install it from the EKS UI (Add-ons tab) or with the CLI (refer to this guide for more details)
3 — Why is it important?
- Enables the Kubernetes Service abstraction
- Provides load balancing for pod-to-pod communication
- Manages network rules for cluster-wide communication
- Essential for implementing Kubernetes networking model
4 — When did it become required?
For EKS, it became an official required add-on aligning with the broader industry move towards externalized cloud provider functionality.
CoreDNS
1 — What is it?
CoreDNS is a flexible, extensible DNS server that serves as the cluster DNS in Kubernetes. It’s responsible for service discovery within the cluster.
2 — How does it work?
1. DNS Resolution : CoreDNS runs as a pod (usually replicated) in the
kube-system namespace.
2. Service Records : It creates DNS records for Kubernetes services,
allowing pods to discover and communicate with each other using domain names.
3. Pod DNS : CoreDNS also manages DNS for individual pods, if configured.
4. Plugins : CoreDNS uses a plugin architecture, allowing for easy
extension and customization of its functionality.
3 — How to install it ?
It should be installed on a newly created EKS cluster and if not you can either install it from the EKS UI (Add-ons tab) or with the CLI (refer to this guide for more details)
4 — Why is it important?
- Enables service discovery within the cluster
- Allows pods to communicate using human-readable names instead of IP
addresses
- Supports DNS-based load balancing
- Can be extended to integrate with external DNS systems or provide custom
DNS functionality
5 — When did it become required?
For EKS, it became an official required add-on as part of the broader transition to externalized cloud provider functionality.
Conclusion
AWS VPC CNI, Kube-proxy, and CoreDNS are essential add-ons that work together to provide networking, service discovery, and name resolution capabilities in an EKS cluster. Their transition to required add-ons reflects the broader changes in the Kubernetes ecosystem, moving towards more modular and cloud- agnostic core functionality.
AWS EKS Required Add-Ons: A Comprehensive Guide was originally published in AWS Morocco on Medium, where people are continuing the conversation by highlighting and responding to this story.